In today’s interconnected world, every swipe and tap on an app might seem like a simple action—but behind the scenes, it’s a bustling highway of data, some of it sensitive and personal. With hackers lurking to intercept that information, SSL Pinning has emerged as a hero in the realm of app security. Let’s explore SSL Pinning in a way that’s both informative and fun—because, after all, who said security couldn’t be interesting? 😉
🌐 The Internet and Its Hidden Vulnerabilities
Before diving into SSL Pinning, it's crucial to understand how data moves across the internet. Imagine the internet as an open highway connecting millions of devices. While convenient, it’s also an easy target for anyone aiming to intercept that data. This is where protocols like SSL (Secure Sockets Layer) come into play to protect data in transit—but they aren’t invincible on their own.
- Network is a group of connected computers that are able to send data to each other.
- The term "internet" comes from "interconnected network.”
- The open nature of the internet led to significant security vulnerabilities. Like, data transmitted over HTTP was unencrypted by default.
🔐 What Exactly is SSL?
SSL, now often referred to as TLS (Transport Layer Security), is a security protocol used to protect data exchanged over the internet. It works behind the scenes, ensuring three main things:
- Encryption: Think of it as a lock that scrambles the data so only the intended recipient can unlock it.
- Integrity: SSL ensures that data isn’t altered in transit, so what you send is exactly what the recipient gets.
- Authentication: SSL confirms that both parties in the exchange are who they claim to be.
- SSL 1.0 was never publicly released due to security flaws.
- SSL 2.0 and 3.0 both had their day, but vulnerabilities led to their deprecation.
- TLS 1.0 to 1.3 progressively improved security, with TLS 1.3 being the most robust today.
🛂 What is SSL Certificates: The Passport for Websites
Every time you connect to a website with SSL, you’re greeted by its SSL certificate. Think of it like a passport the website shows to prove its identity.
An SSL Certificate is a digital file that verifies a website identity and enables secure communication using SSL/TLS encryption. This certificate is issued by a trusted authority, known as a Certificate Authority (CA), which includes information about the website's owner, the CA, an encryption key and also ensures the website’s legitimacy.
Here’s why SSL certificates are important:
- They confirm that the site you’re connecting to is legitimate.
- They help create a secure, encrypted channel for data transfer.
But as effective as SSL certificates are, they’re not bulletproof. In fact, they have a notable weak spot…
🔍 The Problem: Man-in-the-Middle (MITM) Attacks
Meet the Man-in-the-Middle (MITM) attack—one of the most notorious threats to SSL security. Imagine you're in a private conversation, but someone sneaks in and starts listening. That’s what a MITM attack does: a hacker positions themselves between you (the client) and the website (server), intercepting the data. They might even modify it or redirect it to a fake server.
This is where SSL comes in. SSL helps to prevent the MITM attacks.
But, SSL alone is NOT ENOUGH to prevent from MITM attack! Because the Standard HTTPS verifies whether the connection is secure but it cannot verify whether you are communicating with the actual server or an intercepted server.
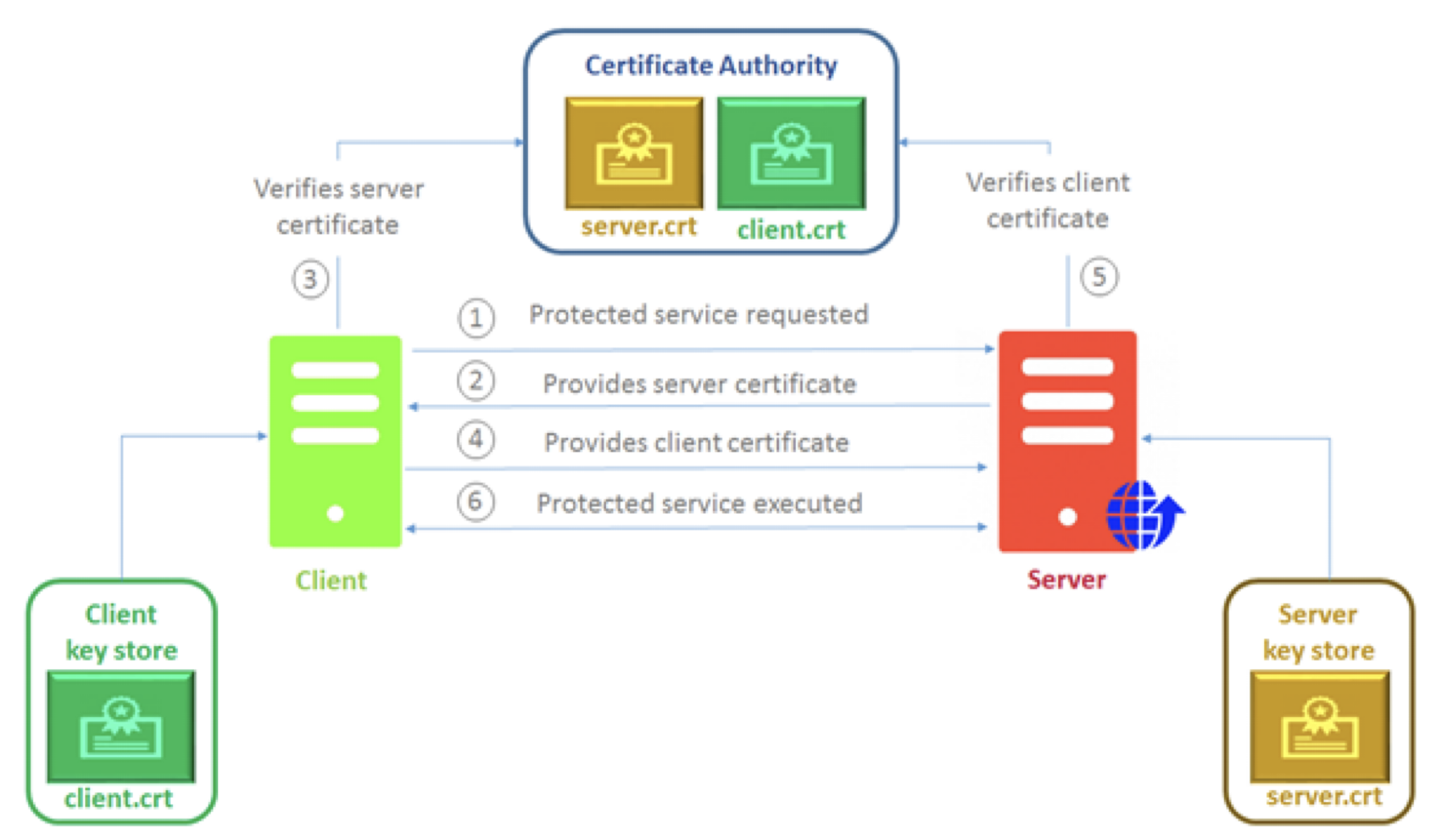
To Understand, let's learn how SSL validates the CA Certificates.
- When a client (e.g., a mobile app or browser) connects to a server over SSL/TLS, the server presents its digital certificate, which is issued by a trusted CA.
- The client verifies this certificate against a list of trusted root CAs stored on the device. This list is maintained by the operating system (e.g., Android, iOS)
- If the server certificate is valid and issued by one of these trusted CAs, the SSL/TLS handshake completes, and an encrypted connection is established.
If an attacker has physical access to the device and modifies the trusted certificate in client device, they can compromise SSL security. This allows them to connect to a fake server that has a valid certificate, enabling them to intercept the data through a Man-in-the-Middle (MITM) attack.
🛡️ Enter SSL Pinning: The Ultimate Defender!
SSL alone may not be enough to fend off an MITM attack, but this is where SSL Pinning comes in! 🔥
SSL Pinning acts as a "checkpoint" between your client (app) and the server, adding an extra layer of validation to verify the server’s identity. Here’s how it works:
- With SSL Pinning, the app hardcodes a specific SSL certificate or public key, so it knows what the "real" server looks like.
- Each time the app communicates with the server, it compares the server's SSL certificate against this hardcoded version. If they don’t match, the app knows something’s fishy and can block the connection!
So, with SSL Pinning, even if a hacker manages to fool your device into trusting a fake certificate, they’ll hit a wall when they try to bypass the pinned certificate. 👊
🛠️ Types of SSL Pinning: What to Pin?
Not all SSL Pinning is created equal! Here are two main types:
- Certificate Pinning 🗂️ With certificate pinning, the app is bundled with the server’s certificate. At runtime, the app checks the certificate presented by the server against this pinned version. If they don’t match, the connection is blocked. Certificate pinning is a simple but effective technique, especially if the server’s certificate doesn’t change often.
- Public Key Pinning 🔑 In this approach, instead of pinning the entire certificate, the app pins the certificate’s public key. The app compares the server’s key to the hardcoded one in the app. This is often preferred when certificates might need to be updated without changing the public key.
Choosing the right type of pinning depends on your app’s specific needs and how often the certificate might change.
Read this blog to learn about to integrate SSL Pinning on Android apps - https://www.mobiledev.blog/2024/10/secure-android-apps-with-tlsssl-pinning.html
⚠️ SSL Pinning: Be Aware of the Trade-offs!
While SSL Pinning is a fantastic security measure, it’s not a “set it and forget it” solution. Here are a few things to consider:
- Maintenance: If the pinned certificate or key changes, the app needs an update. Otherwise, users might experience connection failures.
- Flexibility: Over-pinning can create compatibility issues, especially if third-party servers are involved, which your app may not control.
- Fallback Mechanism: Without a fallback, SSL Pinning could block legitimate access if the server’s certificate expires or changes suddenly.
That said, the benefits of SSL Pinning in reducing MITM attacks far outweigh these concerns, especially for apps that handle sensitive data.
💡 SSL Pinning in Action: A Simple Workflow
Imagine a banking app that uses SSL Pinning to protect its users. Here’s how it works behind the scenes:
- The Initial Request 📨 The user opens the app and initiates a request to view their bank balance. The app immediately verifies the server’s identity using SSL Pinning.
- Certificate Verification 🔍 The server presents its SSL certificate, and the app compares this against its pinned version. If the certificates match, the app proceeds with the connection. Otherwise, it throws an error, blocking the potentially dangerous request.
- Secure Communication 🔒 With SSL Pinning confirmed, the data exchange proceeds through an encrypted channel, safe from prying eyes.
Read this blog to learn about to integrate SSL Pinning on Android apps - https://www.mobiledev.blog/2024/10/secure-android-apps-with-tlsssl-pinning.html
🚀 Conclusion: Securing Your App with SSL Pinning
In the ever-evolving world of cybersecurity, SSL Pinning is a powerful way to keep your app’s data safe. It’s an extra layer of defense that, when implemented well, protects users from sophisticated attacks. So, if you’re building an app that handles sensitive information, SSL Pinning might just be the security upgrade you need!
Remember, a safe user is a happy user. So, go forth and secure your apps with SSL Pinning! 🔐













Post a Comment